- (+1) 571-466-8064
- Washington, DC
Related Topics
Frequently Ask Question
This Cybersecurity FAQ consists of Frequently Asked Questions related to cybersecurity and related topics.
Cybersecurity is the practice of protecting computer networks, systems, hardware, software or electronic data from being stolen or damaged by incoming digital attacks(cyberattacks). Cybersecurity can also be described as the collective of methods, technologies, and processes to help protect the confidentiality, integrity, and availability of computer systems, networks and data, against cyber-attacks or unauthorized access.
A cyber attack is an offensive action by a malicious actor that is intended to undermine the functions of networked computers and their related resources, including unauthorized access, unapproved changes, and malicious destruction. It can lead to loss or damage to important electronic data such as customer and employee information, potentially sabotaging customer-employee relationships. In addition, damage to computer software and hardware can incur extra expenses while also causing loss of income as services offered electronically can be shut down. These dangers, coupled with the possibilities of extortion losses and damage to companies' reputations, emphasize the importance of cybersecurity for any business that depends on computer networks.
Cyber-attacks come in a wide variety. The following list highlights some of important ones that criminals and attackers use to exploit software:
- Malware
- Ransomware
- Injection attacks (e.g., cross-site scripting, SQL injection, command injection)
- Session management and Man-in-the-Middle attacks
- Phishing
- Denial of service
- Privilege escalations
- Unpatched/Vulnerable software
- Remote code execution
- Brute force
The differences among the terms cyberattack, cyber warfare, cybercrime, and cyberterrorism are best explained in terms of their actor (perpetrator) and attack effect (equivalent result) characteristics, as shown in the following table.
| Classification | Actor | Attack Effect Equivalency |
|---|---|---|
| Cyber Attack [Generic] |
TBD | TBD |
| Cyber Warfare [includes Cyber Espionage, Cyber Sabotage] |
State [Nation] |
War Act |
| Cyber Crime | Non-State (individual/organization) | Criminal Act |
| Cyber Terrorism | Non-State (individual/organization) | Terrorism Act |
Although most people understand what spamware is without a formal definition, the most common malware types (viruses, worms, trojans, and bots) are frequently confused by computer experts (who are not cybersecurity experts) and regular computer users alike. The following table summarizes the similarities and differences among viruses, worms, trojans, and bots.
Attacks are evolving swiftly and security solutions shouldn't depend on static and hard-coded (programs/solutions) for a fixed set of events. CyberGasha offers tailored security solutions, playbooks and runbooks to deal with all manner of cyber incidents. Our services allow you to remain in control, ready to adapt and adjust the response workflow.
| Malware Type | Require Host File | Self-Spreading | Appears Harmless | Can Carry Harmful Payload | Can Commo With CMD | Can Attach OS Kernel |
|---|---|---|---|---|---|---|
| Virus | Yes | No | N/A | Yes | N/A | No |
| Worm | No | Yes | N/A | Yes | N/A | No |
| Trojan | Yes | No | Yes | Yes | N/A | No |
| Bots/Botnet | No | Yes | N/A | Yes | N/A | No |
| Spyware | No | No | N/A | No | Yes | No |
| Rootkit | N/A | N/A | N/A | Yes | N/A | Yes |
| Blended Threat | Yes | Yes | Yes | Yes | Yes | Yes |
Cyberattacks are cheap to perpetrate, happen every day and can be a huge expense to recover from. Data breaches cost companies millions of dollars. Yet, cheap, relatively easy-to-use off-the-shelf hacking tools make the barrier to entry for cybercriminals incredibly low. In 2017, the credit reporting agency Equifax was hacked. It resulted in 146.6 million Americans having their personal data exposed and the cost to Equifax as a company was massive. To date, the breach is expected to cost Equifax around $600 million to resolve - this includes lawsuits. But this is not the only losses Equifax experienced after the breach. The company's share price drop, post-breach, resulted in $4 billion being wiped off their market value. The cyber-cost equation has many variables:
- Lost revenue due to downtime
- Loss of customer confidence in your company - a study has showed that 86% of people would be less likely to deal with a business after a data breach.
- Share price or market value drop
- Damage to your IT infrastructure - 78% of companies experience service degradation after an attack
- Costs associated with managing exposed customer data
- Attorney fees from lawsuits
- Ransom money (if an incident involves ransomware) - ransoms, if paid, can run into the many thousands of dollars
- Losses due to stolen proprietary information of intellectual property (IP)
Some or all of these issues can be felt by a company, post-attack. Many of them are long-lasting and complex. Costs incurred can mean communicating with customers as well as regulatory bodies. This takes time from your business and means paying attorney costs.
CyberGash recognizes cybersecurity isn't a cheap investment and will rigorously consult with you team to identify the appropriate solutions that will meet your requirement.The simple answer is yes. Cybercriminals do not discriminate. All companies, everywhere, across all sectors, are a target for cyber crime. Every industry, from manufacturing to healthcare to government to financial to education, is being affected. Cisco’s 2018 SMB (small-medium businesses) Cybersecurity Report looked into the impact of cybersecurity threats on organizations with fewer than 250 employees. The report found that 53% of SMBs had experienced a cyber-attack. If your company suffers a breach, data is exposed, systems are potentially damaged, and employees lose work time. All of this equals money, reputation, and time lost.
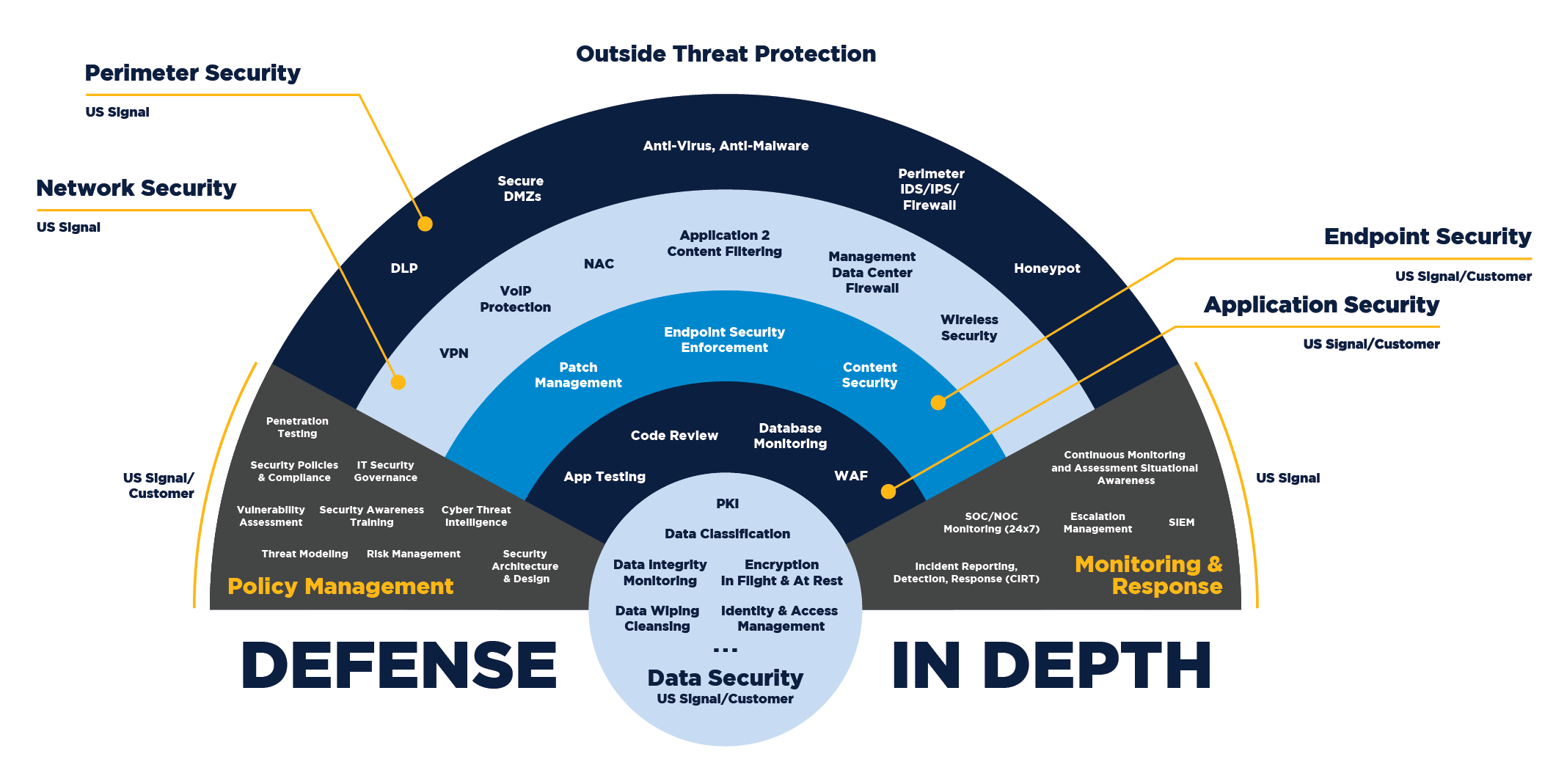
CyberGasha assists in identifying the risk as well as in the determination of appropriate management actions and established priorities for managing and implementing controls to protect against those risks.Good Cyber hygiene implements layers of security. Defense-in-depth is an information assurance strategy that provides multiple, redundant defensive measures in case a security control fails or a vulnerability is exploited. It originates from a military strategy by the same name, which seeks to delay the advance of an attack, rather than defeating it with one strong line of defense. Layering security defenses in an application can reduce the chance of a successful attack. Incorporating redundant security mechanisms requires an attacker to circumvent each mechanism to gain access to a digital asset. For example, a software system with authentication checks may prevent an attacker that has subverted a firewall. Defending an application with multiple layers can prevent a single point of failure that compromises the security of the application.
CyberGasha has experience in deploying a defense-in-depth security architecture based on controls that are designed to protect the physical, technical and administrative aspects of your network.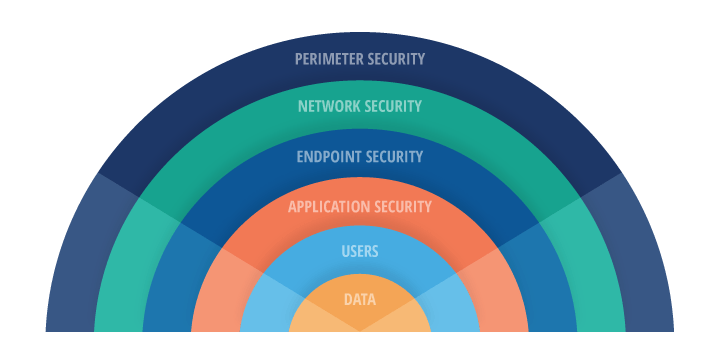
Customers and employees represent a large potential attack surface for every organization. People are the assets of an organization and you need to invest in them continually. As your infrastructure will be vulnerable if it doesn’t get patched, people would pose the greatest risk if they don’t get trained continually. While you can set up any manner of systems to protect your business with cybersecurity, the truth is that many attacks target you where you’re most vulnerable: your employees. Understanding how to train employees for cybersecurity is essential for every company operating digitally. Here are the best practices to help you train your employees for cybersecurity.
- Make Cybersecurity Awareness a Priority
- Emphasize Password Security Trainings and Best Practices
- Train Employees to Recognize Phishing and Social Engineering Attacks
- Make Cyber Security a Part of Onboarding
- Conduct Phishing Drill
- Invest in Employee Training
Advanced Persistent threats (APT) is a targeted attack which has a multiphase step to compromise a network while being undetected and stays undetected while collecting a large volume of data for a long period of time. Advanced Persistent threats (APT) can be an attack campaign performed by individuals, groups of intruders or even nation-sponsored. Advanced Persistent threats (APT) are complex and vary from attack to attack. They can use a zero day attack to phishing email. Like other attackers, APT groups try to steal data, disrupt operations or destroy infrastructure. Unlike most cyber criminals, APT attackers pursue their objectives over months or years. They adapt to cyber defenses and frequently retarget the same victim. The following can be used to characterize Advanced Persistent threats (APT)
- Financial and human resources
- Sophisticated technical tools
- Organization and discipline
- Clear, defined objectives
- Use of social engineering